ECQ Success Stories: CT Link Remotely Sets up Audio Conferencing Option on Teams

Right now, there are little to no physical meetings happening due to the need for us to practice social distancing. This has caused a spike into companies looking to put their meetings in the virtual space where they can be safely conducted. To others, however, video conferencing is not feasible for various reasons. One of […]
ECQ Success Stories: CT Link Services Remotely Restores Client’s Web Services

Disruption to your business can happen without any notice. This was felt by everyone when the enhanced community quarantine (ECQ) was suddenly implemented last March 2020. Companies were forced to adopt a Work From Home program where servers are expected to be always available even when unattended. Client Challenge A couple of days into the […]
Enhanced Quarantine: Protect your Philippine Business from Covid-19 Disruptions
With the Covid-19 impacting almost everyone, companies are reviewing their business continuity strategy during this unplanned disruption. To keep the business up and running, organizations must take a more comprehensive approach encompassing both organizational measures and technologies to minimize disruption, maintain security, and support uninterrupted productivity for users and teams. Best practices for a complete […]
Security Advisory: Malicious Attacks using COVID 19 Phishing Emails
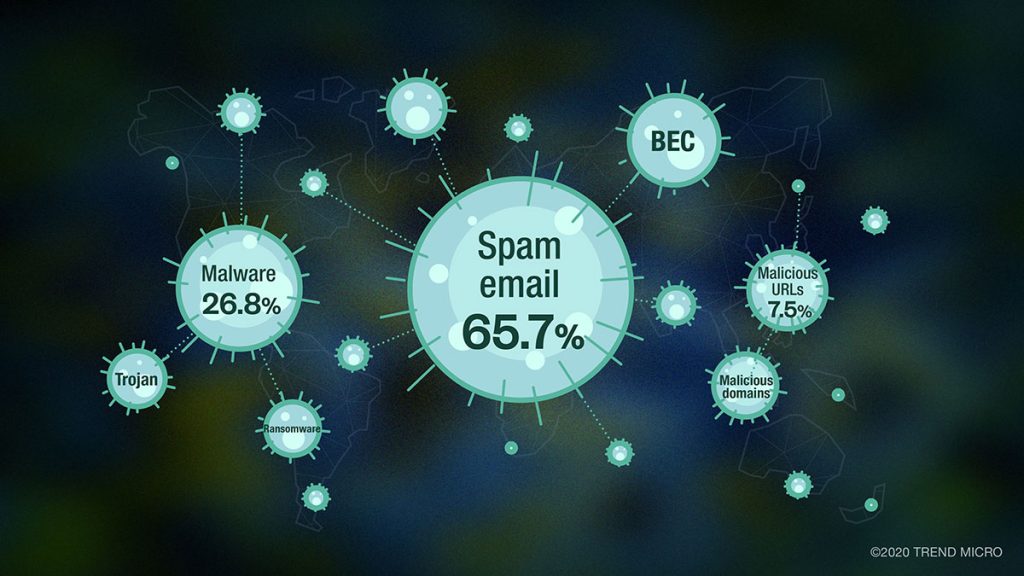
Due to recent events, many of us have had to do significant life changes be it personal or work related. This has affected many of us globally and even created a trend that many are using to their advantage, such as people making profit off shipping masks to other countries. So, it comes to no […]
Five tips from Microsoft Detection and Response Team to minimize Advanced Persistent Threats
Microsoft’s Detection and Response Team (DART), in an effort to encourage the use of better security practices, is planning on sharing its experiences wit customers to let others know the methods of hackers. One particular customer story just shows how some organizations are still lax when it comes to security as they had 6 different […]
CT Link is Here to Support You!
To all Our Valued Clients: As the government announces the suspension of work due to the current health crisis, CT Link would like to reassure you that we are still committed to supporting your needs during this difficult time. We understand the impact that this pandemic has brought upon businesses and individuals alike, and we […]
