
Vulnerability Assessment and Penetration Testing (VAPT) Services
As businesses grow more dependent on digital systems, they also face increasing risks from cyber threats. Identifying and addressing vulnerabilities before attackers exploit them is essential to safeguarding your operations, reputation, and customer trust. That’s where Vulnerability Assessment and Penetration Testing (VAPT) comes in.
What is VAPT?
VAPT is a combination of two critical processes in cybersecurity: Vulnerability Assessment and Penetration Testing. While both aim to strengthen your defenses, they focus on different aspects of security:
- Vulnerability Assessment identifies weaknesses in your systems, networks, or applications that could be exploited by attackers.
- Penetration Testing simulates real-world attacks to determine if these vulnerabilities can be exploited and how much damage they could cause.
Together, these methods provide a comprehensive picture of your organization’s security posture, helping you prioritize risks and take action to mitigate them.
Types of VAPT Assessments
Understanding the different types of VAPT assessments helps you determine which approach best addresses your specific security needs.

Network-Based Testing
This approach targets your organization’s network infrastructure, such as routers, switches, and firewalls. It aims to uncover vulnerabilities that could lead to unauthorized access or data breaches.

Host-Based Testing
Individual devices such as servers and workstations are assessed for weaknesses in operating systems, configurations, and applications.

Application-Based Testing
Applications are a common entry point for cybercriminals. Testing web and mobile applications ensures that vulnerabilities like insecure code or weak authentication are identified and addressed.

Database Testing
Since databases often store sensitive and valuable data, this testing focuses on identifying issues like permissions misconfigurations or outdated patches that could lead to data breaches.
Why VAPT is Essential for Businesses
Identifying and Prioritizing Security Gaps
VAPT doesn’t just point out issues; it helps you understand which vulnerabilities pose the most significant threats. This insight ensures your resources are directed where they’re needed most.
Enhancing Long-Term Security Planning
VAPT provides a roadmap for future improvements, enabling you to plan and implement security measures systematically over time.
Strengthening Compliance
Efforts Meeting regulations such as the Data Privacy Act (DPA), PCI DSS, and ISO 27001 is critical for many businesses in the Philippines. VAPT helps ensure your security measures align with these requirements.
CT Link's VAPT Approach
At CT Link, we use a modern, AI-powered approach to ensure our VAPT services are thorough and effective. Our methodology focuses on providing continuous insights into your security posture, empowering your business to adapt and improve proactively.

AI-Driven Automation
We use advanced AI tools to replicate real-world cyberattacks. This approach uncovers vulnerabilities that traditional methods might miss while saving time and resources.

Continuous Testing
Security threats don’t wait, and neither should your defenses. Our ongoing testing ensures your organization is prepared to face new challenges as they arise.

Tailored Reporting and Action Plans
Beyond identifying issues, we provide actionable insights to help you prioritize and resolve vulnerabilities effectively.

Real-World Attack Simulations
By mimicking the techniques used by hackers, we provide a realistic view of your security gaps, enabling you to strengthen critical areas before they are exploited.
Simulating Real-World Attacks
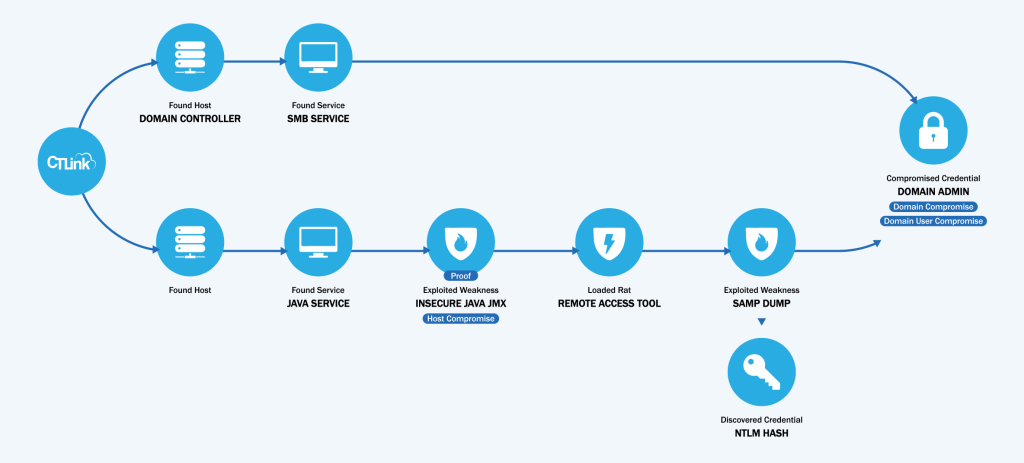
In cybersecurity, threats are rarely static. Attackers move swiftly, exploiting weaknesses in systems, applications, and networks to infiltrate your organization. The visual above shows a real-world attack path exploiting SMB and Java JMX vulnerabilities, resulting in the compromise of Domain Admin credentials — the keys to your digital kingdom.
Imagine if this were your network.
CT Link’s Vulnerability Assessment and Penetration Testing (VAPT) services simulate these real-world attacks to reveal vulnerabilities before malicious actors can exploit them. By identifying weak points and simulating exploits like the one shown, our VAPT process helps you:
- Discover critical security gaps.
- Simulate actual attack paths.
- Prioritize the most urgent risks.
- Strengthen defenses proactively.
Our AI-driven approach and real-world attack simulations ensure that your systems are tested against modern threats, giving you a clear, actionable path to improved security.
VAPT Process
Our process follows a structured and systematic approach to ensure comprehensive security assessments and actionable outcomes:
Planning and Scoping
Defining the purpose and scope is crucial for a focused VAPT. During this phase, we collaborate with your team to set clear objectives, determine the systems, applications, or networks to be assessed, and establish boundaries to avoid disruptions to your operations.
Information Gathering
Using a mix of automated tools and manual techniques, we collect detailed information about your IT environment, including system configurations, network architecture, and existing security measures. This phase forms the foundation for a precise assessment.
Vulnerability Assessment
Automated scanners are employed to identify known vulnerabilities in your environment, such as outdated software, misconfigurations, or missing patches. This phase highlights potential weaknesses in your systems, helping you understand your security landscape.
Penetration Testing
Simulating real-world attacks, we use advanced tools and techniques to attempt to exploit the vulnerabilities identified during the assessment phase. This step evaluates the practical risks and potential impact of these weaknesses on your business.
Reporting and Remediation Guidance
After the testing phase, we deliver a detailed report summarizing our findings, including the vulnerabilities discovered, their severity, and tailored recommendations for remediation. Our reports prioritize risks, allowing your team to address critical issues first while planning for long-term improvements.
Continuous Security Improvement
Security is an ongoing effort. While the service can be a one-time engagement, we also offer optional follow-ups to track progress on remediation efforts and provide updated assessments as your security posture evolves. This ensures your defenses remain robust against emerging threats.
By clicking “Submit,” you agree to our Privacy Policy and consent to the collection and use of your personal information as described therein.
