New Vulnerability aLTEr Discovered by Researchers
Researchers from Ruhr-Universität Bochum & New York University Abu Dhabi have recently discovered three types of attacks/vulnerabilities for devices using Long-Term Evolution (LTE) network protocol that cyber criminals can use to steal your data. The researched team has dubbed the attacks as “aLTEr”. With LTE (a form of 4G) as a standard in the mobile […]
Ransomware Lunch & Learn With Cisco!
Ransomware is becoming more prevalent now as more companies are starting to have their networks infected with these disruptive malware. With this in mind, Cisco has been improving their security portfolio to keep your IT infrastructure same from these malicious malware attacks. Learn more about it from our Cisco experts on July 17, 2018 at […]
Meraki Wireless Health is Now in Beta!
Last January Cisco announced that they would be adding an exciting new feature for Meraki, the Meraki Wireless Health. In essence, Wireless Health is a powerful heuristics engine which can promptly find errors which are affecting the end users experience across multiple stages of their connectivity, which includes association, authentication, IP addressing and DNS availability, […]
Wireless Big Data: An Exclusive Tech Update with Cisco and Pure Storage
Wireless big data has the ability to provide in-depth information and analytics which allows operators to facilitate data-driven approaches for network optimization and operation. CT Link Systems, Inc. in partnership with MSI-ECS Philippines will be hosting a tech update on Cisco (specifically on Cisco Meraki) and Pure Storage this coming June 14, 2018 at M […]
Increase your Business Network Visibility with Cisco Meraki!
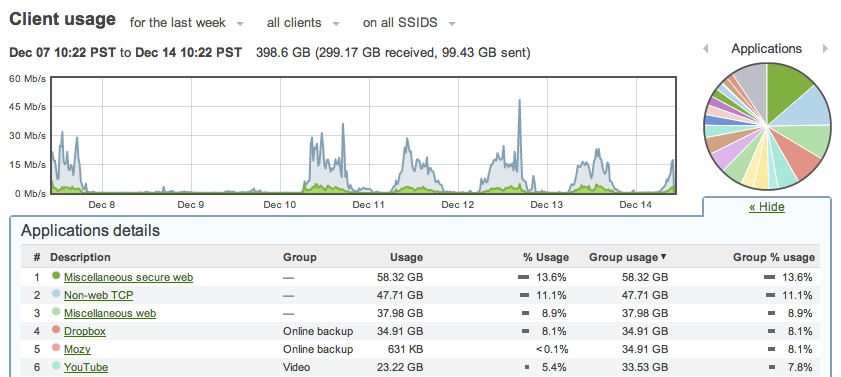
Does your business have enough bandwidth? Many businesses today are looking for ways to upgrade their current bandwidth because of user feedback, they complain mostly about slow browsing speeds. Little do they know that there is a certain user in the office that is “torrenting” on the network, which results to bandwidth hogging and can even […]
Security Advisory: Meltdown & Spectre Zero day Vulnerabilities
Over the past few days, you may have heard of the new vulnerabilities that has been uncovered, Meltdown and Spectre. These vulnerabilities affect all modern processors, meaning your business machines and even personal gadgets that use processors are affected which puts you in risk of potential attacks. Below is a brief explanation of what exactly […]
