Security Advisory: Vulnerabilities found on DHCP and Microsoft Exchange
Microsoft released patches for vulnerabilities that were actively being exploited via their regular security release on the last few months of 2018. They released 49 security patches and two advisories for 2019, seven were vulnerabilities rated as critical while 40 were important. The highlight of these vulnerabilities is regarding to Windows DHCP Client (CVE-2019-0547), this allows a […]
3 Important Questions to remember when securing your SAP Environment
Are you sure you are securing your SAP environment properly? With the sensitive data stored in most SAP systems (HR, financials, and even more important, customer data), it would not be an exaggeration to say that it would be the main priority of attacks of cyber criminals. This doesn’t mean that SAP does not prioritize […]
Managed Detection and Response: Helping to Fill in Gaps of Business Security
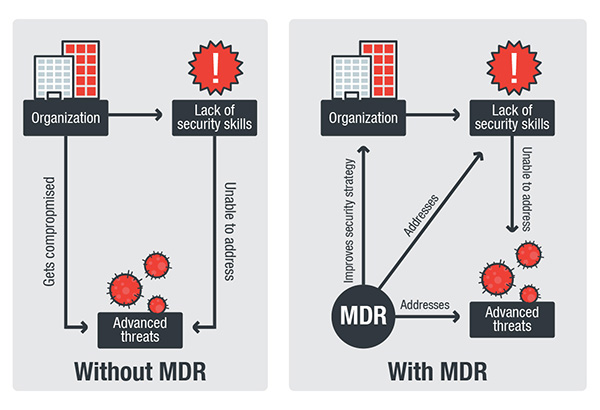
Managed detection and response (MDR) is an outsourced service that provides organizations with threat hunting service and responds to threats once they are discovered. What sets it apart from other security services is the human element in which security providers provide access to their security resources such as their researchers and engineers who will now […]
New Exploit “Faxploit” Poses as a Security Risk for HP OfficeJet All-in-One Printers
Security researchers have recently demonstrated at the security conference DEF CON 2018 a vulnerability that can be exploited via HP OfficeJet All-in-One Printers. It is being dubbed “Faxploit” by the researchers, Eyal Itkin and Yaniv Balmas. The attack takes advantage of security flaws in the implementation of the fax protocol used by OfficeJet printers, making […]
Security Tips: Different Business Email Compromise (BEC) Schemes to Watch Out For

Business Email Compromise (BEC) Schemes In the past few years, millions of dollars have been lost to fraudsters and scammers. However, not all have been lost through malware attacks such as ransomware. Business email compromise (BEC) schemes are sophisticated attacks focused mostly on companies who do wireless transfers frequently. The FBI have estimated that nearly […]
Malware VPNFilter is on the Rise as Infected Routers Increase Globally
On May 24, a report was published by security researchers upon the discovery of a group who had infected more than 500,000 home and small-enterprise routers in at least 54 countries with their malware VPNFilter. This malware can attack, collect research, steal key credentials, monitor SCADA protocols, and install a kill command to destroy your device via your […]
